Google Threat Analysis Group (TAG) released a report on 11 November 2021, which mentioned that in August this year, they discovered watering hole attacks targeting visitors to Hong Kong websites of political media outlet.
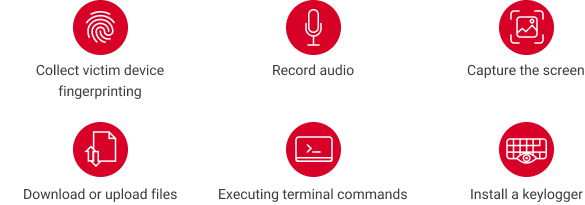
Hackers took advantage of the vulnerability of iOS and macOS to install a back door called ‘MACMA’ into those websites. They then were able to upload/download files, take screenshots etc. through the back door. Google analyst said that the payload code was high quality with sophisticated design, they believed this threat might be supported by the state.
What is ‘watering hole’ attack?
Watering hole attack is a designed attack that target specific groups. Hackers will analyze users' online preferences, search for vulnerability in the websites, and implant malicious code into the websites. When the victim connects to those websites, the malicious code of the website will interact with the user's browser, and then invade the user's system. If the operating system of victims’ device is not up-to-date, they will be more vulnerable to attack.
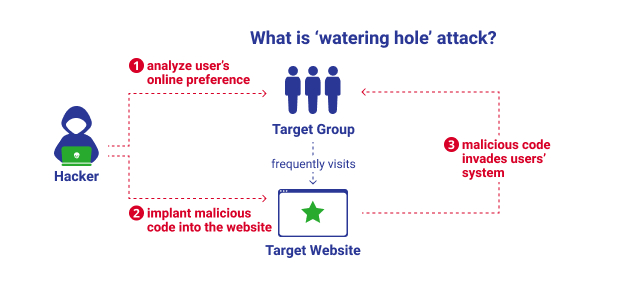
Take the case as an example, hackers have exploited known vulnerabilities to attack the macOS Catalina system, and install a back door on victims’ devices that visited the compromised websites. Catalina was launched in October 2019, while the latest version Big Sur was launched in November 2020. In other words, users will potentially be attacked if they do not use the most updated operating system.
What are the consequences?
How to fix?
- Apple released a patch to protect users from these attacks. Users should update their operating system to the latest version immediately.
Since the hackers attack through 0-day vulnerability, it is difficult for ordinary users to discover security problems. It is recommended that users update the operating system regularly.
It is recommended that users set up Two Factor Authentication (2FA) for their bank accounts, social media accounts etc. to avoid hackers directly obtaining the right to use the accounts.
